Harnessing AI for Cyber Resilience: Turning the Tables on Evolving Threats
By Isaac Mao
Nov. 2024
In my 2021 article “An Animal Farm of Disinformation” for PEN, I explored how adversaries exploit open technologies and free communication channels to weaponize disinformation, eroding public trust. Today, with the rise of AI-generated deepfakes and synthetic media, such campaigns have reached new heights of sophistication, manipulating populations at scale. Countering these threats demands intelligent, autoscaling systems that operate under the strategic guidance of human expertise.
The i-SOON (安洵) leak of February 2024 confirmed these observations—and took them a step further. It was not merely a harrowing revelation; it was a rupture. Within the trove of exposed documents lay a stark duality: a map of sophisticated cyber espionage tactics and the vulnerabilities and inefficiencies of the attackers themselves. Employee chat logs unexpectedly revealed confusion over target lists, recruitment challenges, and candid admissions of operational shortcomings. This breach illuminated a fundamental truth: even the most formidable adversaries have limits. The lesson is clear—just as attackers evolve, so must defenders learn, adapt, and anticipate. .
Evolving the Battlefield: Why Scalability Matters
Cybersecurity today resembles a battlefield laden with threats, expanding endlessly into the digital horizon. Generative AI crafts persuasive deceptions; ransomware paralyzes critical infrastructure; and misinformation destabilizes democracies. The i-SOON case amplifies these realities, revealing how adversaries exploit every conceivable gap—from supply chains to human psychology.
Yet therein lies both the challenge and the promise. To confront these threats, we must abandon piecemeal defenses in favor of scalable strategies that grow stronger with every attack they counter. Scalability is the keystone; it aligns cybersecurity with economic efficiency. A scalable strategy embraces AI’s potential to simulate, defend, and educate—a framework where technology, data, and human ingenuity converge into an ecosystem that not only withstands but flourishes under pressure.
The Four Tiers of Resilience
Here, I propose a four-tier framework for sustainable cybersecurity: Tier 0: The Data Lakehouse, Tier 1: The Simulator, Tier 2: The Defender, and Tier 3: The Educator. Each tier is powered by advanced AI technologies, from machine learning models that process vast datasets to language models designed for education and engagement.
Much like the revolutionary breakthrough of Generative Pre-trained Transformer (GPT) architecture in 2017, this framework thrives on the interconnectedness of its components. Each tier informs and strengthens the others, creating a feedback loop of continuous learning, adaptation, and refinement. Over time, this synergy evolves into a holistic, autonomous system—one that becomes smarter, more agile, and increasingly resilient with every iteration.
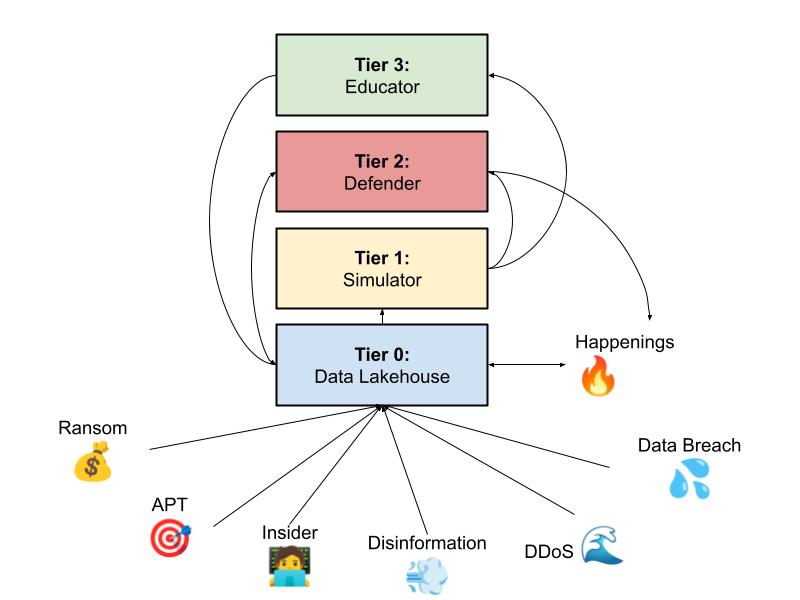
Tier 0: Data as the Lifeblood
At the heart of this framework lies a robust data infrastructure—the lifeblood of sustainable cybersecurity. Data streams in from every frontier—routers, IoT sensors, threat logs, experts’ annotations, and both public and private networks—feeding the AI’s insatiable need for context. By leveraging modern Data Lakehouse pipelines, this infrastructure seamlessly ingests real-time data streams alongside batches of historical data.
This infrastructure operates continuously, processing and integrating data 24/7 to provide “golden analytics” that empower both human analysts and AI models. Its outputs—clean, contextualized, and actionable intelligence—serve as the foundation for machine learning and real-time actions at higher tiers.
Tier 1: The Simulator – Illuminating the Unknown
Building upon the robust data infrastructure and foundational models trained in the Data Lakehouse, the Simulator tier emerges as a fleet of AI-driven agents that vividly demonstrate what threats look like. These simulators operate not as reactive bystanders but as proactive analysts and strategists, anticipating threats before they materialize. By emulating complex attack patterns and integrating human expertise, they transform hidden vulnerabilities into actionable insights.
Inspired by real-world incidents—such as StuxNet, the SolarWinds attack, and the APTs exposed by the i-SOON leak—the simulators reconstruct intricate attack chains while seamlessly informing human experts of their findings. (I recall spending three days analyzing StuxNet’s code; now, with well-defined prompts, AI agents deliver similar insights in under ten minutes.) From ransomware campaigns targeting critical infrastructure to phishing schemes leveraging generative AI, these simulators recreate attack scenarios in dynamic, risk-free environments. Each simulation not only illuminates the shadowy paths adversaries might take but also helps organizations identify weak points, spawn variants, and preemptively fortify their defenses.
Tier 2: The Defender – The Core Immune System
Next tier is the Defender, which emerges as the immune system of the cybersecurity framework—a steadfast guardian that identifies, responds to, and neutralizes live threats in real time. Where simulators chart potential vulnerabilities and offer the best solutions, the AI-driven defenders act decisively, deploying an arsenal of tools such as load balancers, honeypots, endpoint isolation protocols, and more. These agents, like precision-engineered machines, operate tirelessly, attuned to the faintest whispers of anomalies.
Armed with shared algorithms that continually refine their detection capabilities, the defenders stand ready to counter ransomware encryptions, quarantine compromised endpoints, and dissect malicious activity at speeds far beyond human capacity. Their mission is not merely to endure the barrage of attacks but to intercept and dismantle them before they can inflict harm, preserving the integrity of the entire system.
The i-SOON case hinted at how attackers falter due to inefficiencies and poor coordination. In contrast, the Defender tier thrives on adaptability, seamlessly integrating knowledge into its operational arsenal. It becomes a self-improving bulwark against evolving threats, dynamically adapting to the ever-changing landscape of cyber warfare. Together with its sister tiers, the Defender transforms cybersecurity into an active, robust, and scalable ecosystem—one that learns, evolves, and endures.
Tier 3: The Educator – The Keeper of Social Knowledge
Rooted in the philosophy of Sharism, the Educator emphasizes the power of shared knowledge and collective resilience. By leveraging generative AI, this tier tailors its teachings to diverse audiences via natural interfaces(like chatting), empowering individuals and organizations to recognize phishing attempts, discern misinformation, and adopt robust digital hygiene practices.
Unlike static awareness campaigns, the Educator adapts. For a young professional, it might simulate a phishing email(of course it’s generated by AI) to teach them how to be vigilant; for a policymaker, it could explain the geopolitical nuances of cyber risks. Through these personalized approaches, the educator demystifies cybersecurity, making it accessible to all.
From Vision to Reality
Europe, with its pioneering GDPR framework, is uniquely positioned to lead the charge toward ethical and effective AI-driven cybersecurity. By demonstrating that privacy and security can coexist, Europe sets a global benchmark for responsible innovation. Initiatives like ENISA’s CSIRTs Network exemplify the potential of collective intelligence, where cross-border collaboration amplifies efforts to combat evolving threats.
Also, the open-source intelligence (OSINT) community plays a critical role in democratizing access to tools, insights, and best practices. Open-source civic technologies, with their transparency and adaptability, enable this framework to work bottom-up, empowering individuals and organizations to take an active role in securing the digital landscape.
Toward a Future of Resilience
The i-SOON leak serves as both a wake-up call and a call to action: to embrace AI’s transformative power to simulate, defend, and inform, and to turn vulnerabilities into opportunities for growth and resilience. This four-tier framework embodies evolutionary resilience—a dynamic, living system that evolves alongside threats, continuously adapting and strengthening with each challenge. ⬛
